Field Note: Handbook vs Terrain – When Constraint Forecasting Failed and Indications Won
Why this note exists
While this archive is not a platform for news or the churn of current events, it is a space for mapping the mechanics that drive them. This note emerged from a recurring period of cogitation (driven by hours of walking and pondering) after colleagues asked me to articulate why I felt a fundamental shift had occurred in recent maritime strike footage. What began as a hunch eventually mapped out to a concrete doctrinal change… the broadcast of the “kill” without the “trophy.” Historically, the mission was validated by showing the result of the law (the trophy). Today, we are seeing the broadcast of the strike itself (the kill) as the primary signal. This is an exercise in identifying a recurring pattern (a diagnostic tool for understanding shifting operational norms) rather than a commentary on any specific current event.
I keep running into a repeatable mismatch in how smart people forecast: one model predicts from rules, institutions, and “how it’s supposed to work.” Another predicts from behavior, incentives, and “how it’s actually being played.” When the environment becomes exception-driven, the second model starts beating the first, even if the first remains morally and procedurally correct.
This field note captures the pattern and provides early warning systems.
What this note is NOT: This is diagnostic, not operational. It shows you how to SEE the pattern. It does NOT show you how to win against it once you’re locked in. If you’re already the target in a Level 3 or 4 environment, creating “friction” just delays the inevitable. The value is in seeing the shadow before the vulture lands – giving you time to exit before the trap closes.
Companion note: This field note documents the symptom and the tripwires. For the underlying mechanism that explains how multiple events can “move together” without provable coordination, see Field Note: Loosely Coupled Power Grabs (
coming late January, 2026).
Field Note: Loosely Coupled Power Grabs
Scope and Limitations
What this field note does:
- Shows you how to recognize exception-driven environments
- Provides early warning tripwires
- Helps you update forecasting models based on behavior vs. words
- Points toward exit strategies
What this field note does NOT do:
- Give you tools to win a fight against resource-asymmetric actors
- Provide legal strategies to resist Level 3/4 extraction
- Guarantee that pattern recognition alone will save you
- Claim the handbook can protect you when institutions are captured
The hard truth: If you’re already locked into a Level 4 displacement pattern or Level 3 legal liquidation, there often IS no winning move within the system. The goal is to see it coming early enough to disengage before the trap closes.
If you’re looking for how to exit, not just how to observe, see the companion piece: “Strategic Decoupling in Exception-Governed Environments.”
Calibration Is Not a Crusade
This note is about forecasting and self-protection, not moral labeling. Traits and incentives can be real and predictive without turning into an obligation to “destroy” anything. Understanding is not excusing, and prediction is not permission.
Key fallacy to avoid: “If a harmful pattern is not rehabilitatable, then good people are obligated to eradicate it.” That conclusion does not follow. Non-rehabilitatable behavior can justify boundaries, containment, and exit without creating a standing duty to hunt.
Think: an invasive snake in Hawaii. If it appears in front of you, the correct move may be to capture or kill it because the risk is immediate and the window is small. That does not mean your new life purpose is snake hunting (sadly, no pith helmet and khaki shorts for you).
Default response ladder:
- Reduce access (limit exposure, tighten interfaces)
- Increase friction (verification, documentation, accountability)
- Disengage (exit before the trap closes)
- Escalate to legitimate authority (when harm is active and you have duty/capability)
Obligation test (when you actually must act): (1) You have direct duty of care, (2) you are uniquely positioned to prevent imminent harm, (3) action is proportional, (4) action is sustainable and does not become an identity trap.
Scene: When They Started Showing the Kill Instead of the Trophy
Something changed in 2025 that caught my attention.
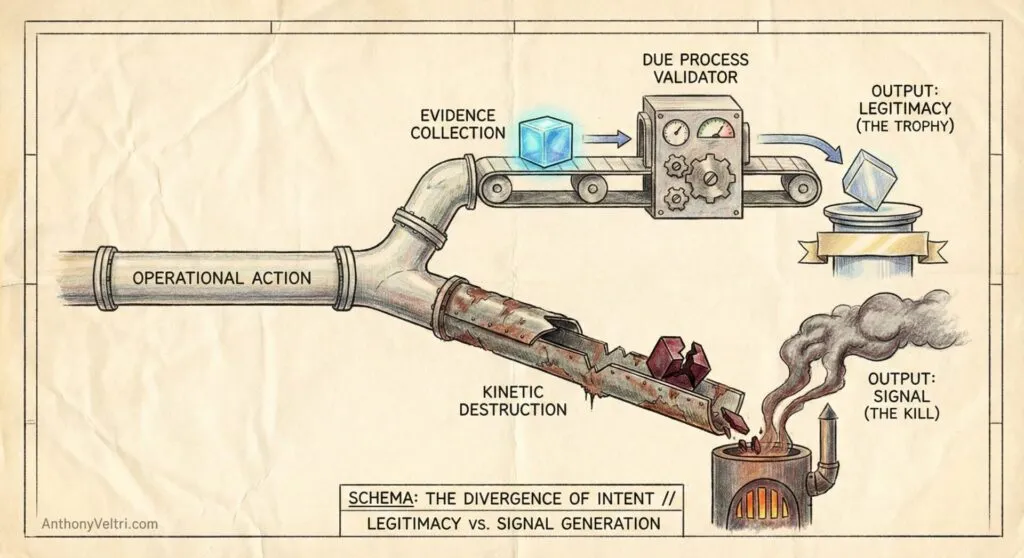
The U.S. was publicizing “counter-narcotics operations” in the Caribbean and Eastern Pacific. They released slick, professionally edited video showing strikes on suspected trafficking vessels.
What struck me was not that force was used. It was what they chose to show.
Normally, law enforcement shows the trophy. Bales stacked. Suspects in custody. Evidence catalogued. The message is “we interdicted and proved it.”
This footage sent a different message.
Standoff weapons. No boarding sequence. No detainees shown. No contraband shown. Just vessels being destroyed from a distance. In a few clips, the framing and timing created the appearance that people in or near the water could be engaged, or at minimum that survival and rescue were not the point.
That is where my ROE question started.
To be explicit: I’m not claiming I know the classified ROE here. I’m observing a public-facing signal shift and asking what kinds of rule-sets could be getting treated as negotiable, or at least operationally deprioritized, for that signal to be publishable.”
The flotsam problem (shipwrecked is a legal status)
Under the law of armed conflict (LOAC) at sea, a shipwrecked person is generally treated as hors de combat. That status exists for a reason: once someone is in the water clinging to debris, the default rule is do not make them the object of attack. The “no shooting survivors on flotsam” norm is not just vibes. It is one of the bright-line moral boundaries the modern laws of war try to enforce. (JAGCNet)
Definition: A person is hors de combat (out of the fight) if they are a combatant who can no longer participate in hostilities due to capture, surrender, or incapacitating injury. Under international law, they must be protected from further attack. (note: if someone is forecasting by looking at the “Handbook” this is what they would expect)
Why cite LOAC in a law-enforcement scenario?
I’m using the law of armed conflict (LOAC) here as a baseline constraint test, not as a claim that this operation is legally “a war.” LOAC is a widely recognized floor for what is off-limits once a person is wounded, incapacitated, or shipwrecked.
If a behavior would be forbidden under LOAC, it is generally even harder to justify under law-enforcement use-of-force standards, where necessity, proportionality, identification, rescue obligations, and post-incident accountability are typically stricter.
So the point is diagnostic: if the public-facing signal starts normalizing destruction-first while survivors are treated as irrelevant or disposable, that’s a red flag under either framework.
And if the operation is not war but law enforcement, the standard is tighter, not looser. The burden is on necessity, proportionality, and accountability. “We can kill you from standoff distance” is not law enforcement messaging.
So when the official product shifts from trophies to kills, it is rational to ask whether the mission is still “interdiction,” or whether it has drifted toward something else: remote punitive destruction (and the new signal that sends).
“What about aircraft?”
People pointed out the Chicago Convention rule that prohibits using weapons against civil aircraft in flight in a way that endangers lives. Chicago Convention, Article 3 bis.
Sure. But the pattern I am watching is not “is there a rule on paper.” The pattern is “what does the public-facing footage normalize.”
When they stop showing trophies and start showing kills, the mission has changed.
That’s when the pattern became clear. The handbook says one thing. The terrain shows another.
Watch for this pattern: When they stop showing trophies and start showing kills, the mission has changed.
Sidebar: “Shipwrecked on Flotsam” is not a free-fire zone (here be dragons)
When footage shows destruction without boarding, prisoners, or recoverable evidence, it raises a follow-on question: what rules apply once people are in the water?
Under the law of armed conflict, the baseline is blunt: wounded, sick, and shipwrecked persons must be respected and protected and should not be made the object of attack. Air University
Distress at sea changes the default posture
Separate from LOAC, maritime operations operate in a world where rendering assistance to persons in distress is a longstanding expectation and often a legal obligation when it can be done without serious risk to the rescuers.
That’s why the public product matters. If the footage repeatedly shows destruction with no boarding, no detention, and no visible rescue posture, the signal being normalized is not “interdiction with accountability,” but “punitive destruction with minimal contact.”
(See: UNCLOS Article 98; SOLAS V/33.)
What would have to be true to justify engaging a shipwreck survivor at all?
In general, only something like continuing direct participation in hostilities could remove that protection. Even then, necessity, proportionality, and feasible precautions still apply.
When does protection drop?
A shipwrecked person is normally treated as out of the fight and should not be made the object of attack. The protection does not become void merely because someone might be armed or might be affiliated with wrongdoing.
Protection could drop only under a narrow condition: continuing direct participation in hostile acts or an immediate, concrete threat that cannot be addressed by feasible alternatives (maneuver, standoff observation, warning, capture, rescue-and-detain).
The diagnostic tell is this: the more an operation relies on standoff weapons and remote destruction, the harder it becomes to justify any engagement with people in the water, because standoff posture usually implies more time and distance to choose non-lethal control options.
Related tell
People cite Chicago Convention Article 3 bis as a bright line for civil aircraft (refrain from using weapons against civil aircraft in flight). Knowvation
The broader point is consistent: law enforcement draws hard lines around lethal force when capture or non-lethal control is feasible, and LOAC draws hard lines around attacking those who are hors de combat (including shipwrecked persons).
The Vulture Pattern: How Coordination Happens Without Conspiracy
This vulture mechanism is the missing layer between handbook forecasting and terrain forecasting. When coordination happens through environmental signals, “prove the conspiracy” becomes the wrong gate. I expanded this mechanism into a standalone companion note, Field Note: Loosely Coupled Power Grabs, including the Two Clocks model and a grouping test for distinguishing patterns from anecdotes.
Here’s where people get stuck. They see the same actors showing up repeatedly to the same “opportunities” and assume conspiracy.
“They must be coordinating. They must be meeting in secret. This can’t just be coincidence.”
But that’s not how the mechanism works.
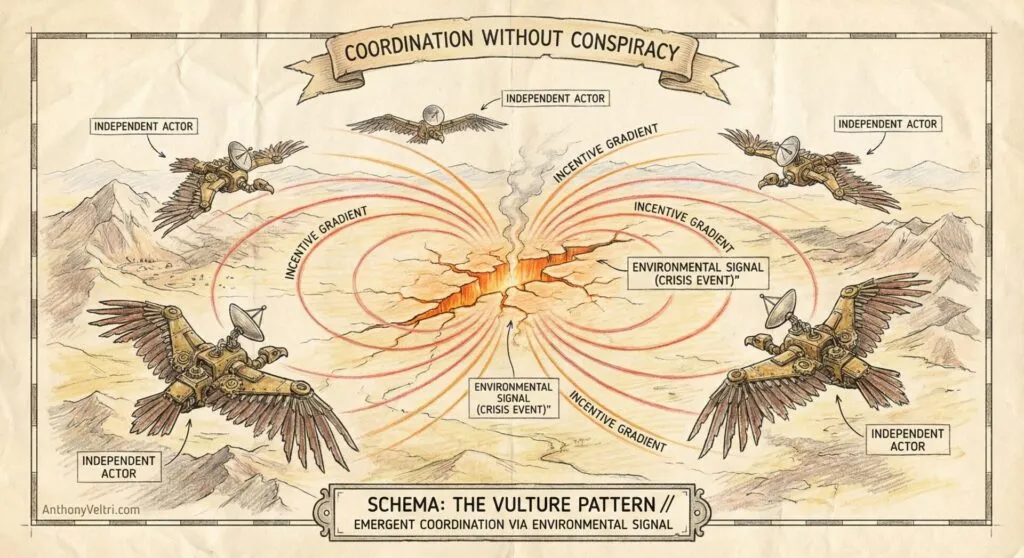
Understanding the Mechanism vs. the Actors
The mechanism operates like biology. The actors are making conscious choices.
Think about vultures. Vultures don’t hunt in packs like wolves. They don’t coordinate attack strategies. They don’t have a leader directing them to carcasses.
Yet they all arrive at the same dead animal, at the same time, and collectively strip it clean.
How? Each vulture circles independently, watching for signs. When one spots something and descends, others see the descent and follow. No meeting required. No conspiracy. Just aligned incentives and shared information signals.
This is the MECHANISM: Coordination through environmental signals rather than direct communication. Biologists call it emergent behavior or stigmergy.
But vultures didn’t choose to be vultures. They’re responding to biological programming.
Private equity analysts DID choose to:
- Attend business schools where predatory strategies are taught
- Join firms that specialize in distressed asset acquisition
- Deploy capital using playbooks refined over decades
- Share successful strategies through professional networks
- Refine their techniques based on what worked before
The Investor Class Mechanism
When disaster strikes – a fire, a hurricane, a financial crisis, a policy change – the same firms show up to acquire distressed assets.
Not because they held a secret meeting to plan the extraction.
Because they all:
- Monitor the same information sources
- Bloomberg terminals showing real-time market data
- Financial news reporting disasters
- Government reports on aid packages
- Investment bank deal flow alerts
- Follow the same incentive structure
- Maximize returns
- Acquire undervalued assets
- Deploy capital where distress creates opportunity
- Use the same professional networks
- Same investment banks connecting buyers to opportunities
- Same law firms handling transactions
- Same conferences where strategies are shared
- Same board interlocks providing information flow
- Internalized the same training
- MBA programs teaching same case studies
- Private equity playbooks standardized
- Professional norms around EBITDA optimization
- Cultural values around “creating shareholder value”
- Respond to the same market signals
- Distressed asset pricing
- Insurance claim data
- Federal aid announcements
- Bankruptcy filings
Sophistication at the Individual Level, Coordination at the System Level
Individual actors are sophisticated:
- Business school graduates who studied these strategies
- Analysts who refine techniques based on results
- Firms that learn from success and failure
- Networks that share “best practices”
The escalating sophistication (direct elimination → plausible deniability → economic weapons → strategic displacement) represents conscious iteration and improvement of extraction techniques.
System-level coordination is emergent:
- No central planner required
- No conspiracy meetings
- Just information flowing through networks
- Aligned incentives creating synchronized responses
This is tacit coordination – behavior that appears coordinated without explicit coordination.
Why This Distinction Matters
You CAN hold individual actors accountable:
- They chose to attend Wharton
- They chose to work at Blackstone
- They chose to weaponize bankruptcy
- They chose to acquire distressed properties
You CANNOT prosecute the swarm itself:
- System operates through legal mechanisms
- Network effects are not conspiracy
- Emergent behavior isn’t illegal coordination
But the collective outcome – systematic extraction, population displacement, wealth concentration – is identical to what a conspiracy would produce.
The result is what matters, not whether someone said the quiet part out loud in a Hollywood-style villain meeting.
The Nervous System Infrastructure
The investor class built infrastructure that enables this coordination:
Sensory Organs (Information Input):
- Financial media (WSJ, Bloomberg, FT)
- Investment banks seeing deal flow
- Government reports (disaster declarations)
- Market data platforms
Distribution Network (Information Flow):
- Board interlocks (same people on multiple boards)
- Professional service firms (law, accounting)
- Conference circuits (Davos, Sun Valley, Milken)
- Alumni networks (Harvard, Wharton, Stanford)
Processing Centers:
- Major PE firms analyzing opportunities
- Investment banks modeling deals
- Consulting firms distributing “best practices”
- Think tanks developing policy frameworks
Execution Mechanisms:
- Capital deployment systems
- Legal structures (LLCs, SPVs)
- Political connections (lobbying)
- Media relationships (narrative control)
This infrastructure is REAL, VISIBLE, and DOCUMENTED:
- Board interlocks are public record
- Conference attendance is known
- Professional networks are visible
- Deal patterns are trackable
Not conspiracy. Structure.
Individual actors built and maintain this structure through conscious choices. The structure then enables coordinated action without requiring coordination.
Watch for this: When the same actors repeatedly appear at the same types of crises, you’re seeing the nervous system activate. Individual sophistication operating through emergent coordination.
Two Models, Different Predictions
When I started asking questions about the maritime strikes, I got two very different types of responses.
Model A: Constraint-First (Handbook Thinking)
“They can’t do that. It’s illegal under international law.”
“Law enforcement requires probable cause and due process.”
“The Law of Armed Conflict prohibits attacking survivors.”
“They’d face international backlash.”
“Congress hasn’t authorized military action.”
“That would violate the Chicago Convention / Geneva Conventions / Maritime Law.”
This model forecasts using:
- Legal authorities and precedents
- Institutional inertia and bureaucratic friction
- Alliance costs and reputational consequences
- “That would be illegal / too costly / too escalatory”
Model B: Behavior-First (Terrain Thinking)
“They’re already doing it. Watch what they do, not what they say.”
“They released footage of the kills. That’s the message they want to send.”
“Standoff weapons mean no imminent threat defense. They chose that approach.”
“No prisoners means no inconvenient testimony.”
“Theater is expanding – Caribbean to Pacific to proposals for other regions.”
“Classification is increasing – legal justifications aren’t public.”
This model forecasts using:
- Revealed preferences (what they actually do)
- Incentive structures and power consolidation logic
- Pattern repetition and normalization
- Capability + intent + rehearsal signals
- Domain creep and exception-becoming-doctrine
The Mismatch
Model A kept saying: “This is unlikely to continue. The constraints will bite.”
Model B kept saying: “This will expand. Watch for aircraft next. Watch for domestic application.”
Model A was describing what SHOULD happen.
Model B was predicting what WOULD happen.
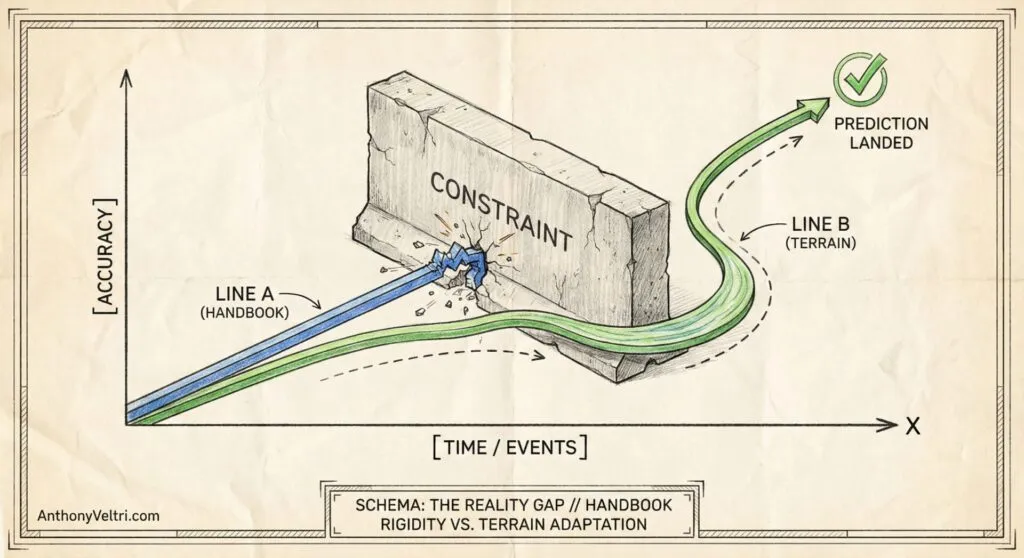
And as events progressed – theater expansion, standoff weapons becoming routine, proposals for even broader authorities – Model B kept landing predictions while Model A kept saying “but that’s not how it works.”
The Pattern: When an actor treats rules as obstacles rather than limits, constraint-first forecasting becomes “Boy Scout Mode” and loses predictive power.
Boy Scout Mode isn’t “rules are dumb.” It’s the specific mistake of believing:
- The other side will behave as if constrained
- Enforcement will be timely and automatic
- Norms will prevent certain moves
- The handbook governs reality
Like a kid who memorized the Scout handbook and assumes everyone else did too.
The mature operator reads the handbook as tools, not destiny.
Watch for this: When your constraint-based model keeps being surprised while your behavior-based model keeps landing predictions, you’re in an exception-driven environment. Update your model.
The Old Saying: Tackle the People, Not the Problem
There’s an old organizational dynamic that rarely gets stated explicitly:
The best way to solve a hard problem is to eliminate the people raising the problem.
Not by addressing their concerns. By making the people themselves go away.
This happens at escalating levels of sophistication:
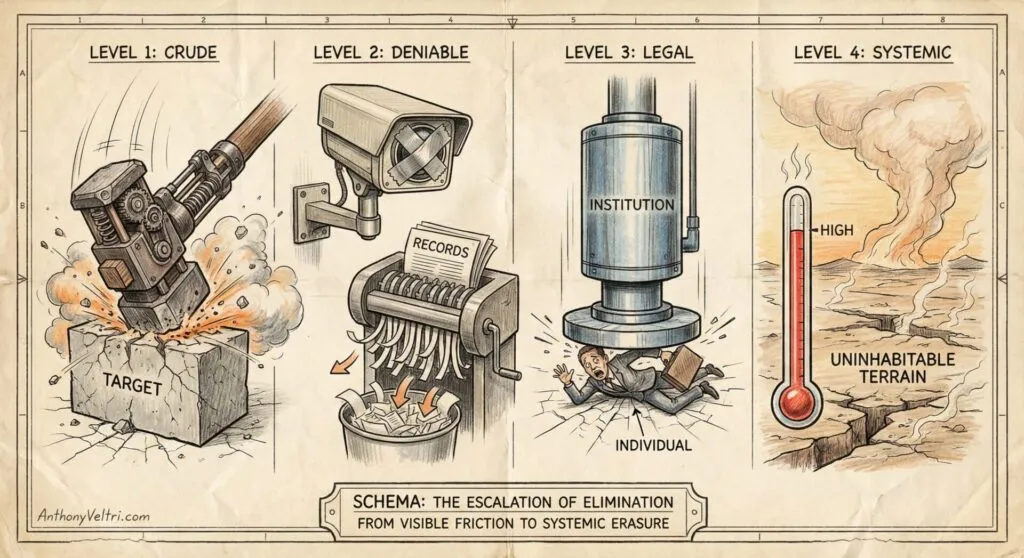
Level 1: Direct Elimination (Crude but Visible)
The pattern: Shoot the messenger. Fire the whistleblower. Arrest the journalist. Kill the witness.
Examples:
- Whistleblowers prosecuted under Espionage Act
- Journalists killed covering cartel activity
- Union organizers targeted for termination
- Survivors of incidents eliminated
Characteristics:
- Visible and crude
- Creates martyrs
- Generates backlash
- Leaves evidence
- Legally risky
Effectiveness: Medium. Works in the short term but creates long-term problems.
Level 2: Plausible Deniability (More Sophisticated)
The pattern: Camera malfunctions. Missing records. Sloppy documentation. Selective amnesia.
Examples:
- Body camera “failures” during critical incidents
- Surveillance footage mysteriously corrupted
- Records destroyed before FOIA requests fulfilled
- Logs incomplete for key timeframes
- Masked agents with no identification
Characteristics:
- Less visible
- Harder to prove intent
- Minimal legal risk
- Creates pattern of “technical failures”
- Protects institutional actors
Effectiveness: High. Difficult to prosecute “accidents.”
Watch for this: When documentation failures consistently benefit one side and harm the other, you’re seeing Level 2 in action.
Level 3: Economic Weapons (Sophisticated and Legal)
The pattern is to use legal and financial mechanisms to eliminate opposition without violence.
While high-profile examples exist (such as the over $110 million in liens filed against Tesla alone and the subsequent bankruptcy of multiple small contractors), this is not just a “Musk” phenomenon. This strategy is deployed across the board by various actors in the investor class.
Search Query for Verification: (If you wish to verify the mechanical pattern, search for: “Tesla construction liens small business bankruptcy” or “private equity legal attrition strategies against contractors.”)
The sophistication of this level is that it is:
- Completely legal (exploiting the slow pace of the justice system).
- Weaponizes the courts against those with fewer resources (resource asymmetry).
- Destroys people economically so they are too broken to continue resistance.
Case Study: Musk and the Contractors
Elon Musk’s companies owed money to small contractors. Rather than pay:
- Delay payment indefinitely
- Force contractors to sue (expensive)
- Bury them in legal motions (more expensive)
- Bleed their cash flow until they face bankruptcy
- Once bankrupt, negotiate with trustee (not passionate business owner)
- Settle for 10-20 cents on the dollar
- Claim gets abandoned, or contractor too broken to continue
The sophistication:
- Completely legal
- No violence
- No visible conspiracy
- Just “tough negotiation”
- Problem (person demanding payment) eliminated
- Solution (debt) resolved for pennies
Over $110 million in liens against Tesla alone. Multiple small businesses forced into bankruptcy. (Note, this is not just Musk
Not because they did bad work. Because they couldn’t afford to fight someone with infinite legal resources.
Other applications:
- Lawfare: Bury opposition in legal fees
- Regulatory capture: Make compliance so expensive only big players survive
- Insurance disputes: Delay/deny until claimants give up or die
- Patent trolling: Threaten litigation until settlement
- Non-compete agreements: Trap workers in positions
Characteristics:
- Completely legal
- Weaponizes the justice system
- Exploits resource asymmetry
- No physical violence needed
- Destroys people economically
- Leaves survivors unable to continue resistance
Effectiveness: Extremely high. Legal system becomes the weapon.
Watch for this: When the same entity repeatedly faces claims that end in bankruptcy or abandonment, you’re seeing Level 3. It’s not bad luck. It’s strategy.
CRITICAL NOTE: This is why “operate like a lawyer” advice fails against Level 3 actors. The legal system IS the weapon being used against you. Legal engagement = stepping into their trap unless you have comparable resources.
Level 4: Hold Your Breath Longest (Strategic Displacement)
The pattern: Make life economically or physically unviable. Wait for people to leave or die. Take what remains.
This is incremental displacement (strategic uninhabitability) – making a place systematically unlivable while maintaining plausible deniability about ultimate intent.
Mechanism:
- Restrict resources (economic pressure, blockades, access)
- Degrade infrastructure (deliberately or through neglect)
- Make basic survival increasingly expensive
- Wait for population to leave voluntarily or die naturally
- Acquire assets once people are gone
- Claim it was market forces or individual choices
Examples:
Maui Fires (2023):
- Fire destroys Lahaina
- Survivors displaced, traumatized
- Real estate investors calling within days
- Aggressive acquisition of distressed properties
- Offers 50-70% below pre-fire value
- Some families received 10-20 contacts per day
- Population can’t afford to return
- Land acquired cheap, redeveloped for wealthy buyers
Private Equity + Single Family Homes:
- Wall Street firms buying residential properties
- Renting back to former owners or new tenants
- Prices increase beyond local wages
- Working class priced out of homeownership
- Entire neighborhoods converted to rentals
- Generational wealth building eliminated
- Population incrementally displaced from economic participation
Rust Belt Deindustrialization:
- Manufacturing jobs moved overseas
- Communities economically devastated
- Population declines through out-migration
- Property values collapse
- Investors acquire distressed assets
- Gentrify select areas, abandon rest
- Original residents gone, new demographic moves in
Post-Katrina New Orleans:
- Hurricane destroys city
- Public housing demolished (not rebuilt)
- Schools privatized
- Working-class neighborhoods not rebuilt
- 100,000+ Black residents never returned
- Wealthier, whiter city emerges
- Heritage Foundation published exploitation plan before bodies recovered
Characteristics:
- No violence required (though sometimes involved)
- Appears natural or like market forces
- Maintains plausible deniability
- Extremely effective at population removal
- Legal framework often facilitates it
- Generational timescales acceptable
- Survivors blame themselves, not system
The sophistication: You’re not forcing anyone. You’re just making it impossible to stay. They “choose” to leave.
Effectiveness: Maximum. Population removed, assets acquired, completely legal, plausible deniability maintained.
Watch for this: When a crisis (natural or economic) is followed by rapid acquisition of distressed assets and the original population can’t return, you’re seeing Level 4.
The disaster isn’t being wasted. It is being mechanically integrated into the extraction sequence. (Some might conclude it’s being exploited.)
The Progression:
Level 1 (Crude) → Level 2 (Deniable) → Level 3 (Legal) → Level 4 (Systemic)
Each level more sophisticated than the last. Each level harder to prove. Each level more effective at eliminating people while maintaining legitimacy.
The United States is currently operating at Levels 3 and 4 domestically, with proposals suggesting Level 1-2 internationally.
Healthcare costs, housing prices, inflation – these aren’t just economic forces. They’re mechanisms that make participation increasingly unviable for larger portions of the population.
Who benefits when people are priced out, bankrupted, or displaced?
Watch where the assets go.
The Pattern Across Contexts: Not Partisan, Structural
This isn’t about one administration, one party, or one country. It’s a pattern that appears wherever power concentrates and accountability weakens.
Watch for the mismatch between words and behavior. Watch for what gets normalized through repetition. Watch for incrementalism that compounds into transformation.
Obama Administration: Drone Program Expansion
The Words:
- “Targeted strikes against imminent threats”
- “Precision warfare minimizing civilian casualties”
- “Legal under Article II authority and AUMF”
- “Transparent and accountable process”
The Behavior:
- Strike volume increased 10x over predecessor
- “Signature strikes” – targeting patterns, not known individuals
- Definition of “militant” became “military-age male in strike zone”
- Casualties counted as combatants unless proven otherwise
- Classification prevented accountability
- “Kill list” maintained with minimal oversight
- Wedding parties, funerals struck based on pattern analysis
The Constraint Model said:
- “Requires imminent threat”
- “Must minimize civilian casualties”
- “Congress must authorize”
- “International law prohibits extrajudicial killing”
The Terrain Model observed:
- Strikes happening based on behavior patterns, not specific threats
- Civilian casualty numbers manipulated through definition changes
- Legal memos classified, not subject to debate
- Theater expanded from Afghanistan to Pakistan, Yemen, Somalia, Libya
- Precedent established for executive unilateral authority
The normalization:
- Started as exceptional counter-terrorism measure
- Became routine foreign policy tool
- Handed to successor as established practice
- Now standard operating procedure across administrations
Pattern recognition: Exception → Repetition → Normalization → Doctrine
This isn’t partisan criticism. It’s pattern observation. The mechanism (executive authority expansion through exception-becoming-routine) transcends which party holds office.
Bush Administration: WMD Narrative vs. Behavior
The Words:
- “Iraq possesses weapons of mass destruction”
- “Imminent threat to United States”
- “Mobile biological weapons labs”
- “Uranium from Niger”
- “We don’t want the smoking gun to be a mushroom cloud”
The Behavior:
- Intelligence community uncertain, dissenting views suppressed
- Evidence curated, contrary evidence ignored
- UN inspectors reporting no findings, given insufficient time
- War launched before inspection process complete
- No WMDs found after invasion
- Troop deployments began before Congressional authorization
- Oil infrastructure secured before civilian infrastructure
The Constraint Model said:
- “UN process must be respected”
- “Congressional authorization required”
- “Intelligence must support claims”
- “International law requires actual threat”
The Terrain Model observed:
- Deployment timelines indicated decision already made
- Intelligence being shaped to support predetermined conclusion
- Dissent being marginalized or ignored
- Alternative motives (oil, regional control) aligned with behavior
- Words used to manufacture consent, not describe reality
The lesson: When deployment schedules, logistics planning, and resource allocation all point one direction while official statements claim deliberation is ongoing, watch the behavior not the words.
Corporate: Disaster Capitalism Across Multiple Crises
The Pattern (Repeatable):
- Crisis occurs (natural disaster, financial collapse, pandemic)
- Emergency declared, normal processes suspended
- Private sector “solutions” presented as only viable option
- Public assets privatized, public services cut
- Reconstruction benefits corporations, not residents
- Original population displaced, new demographic replaces them
Puerto Rico – Hurricane Maria (2017):
The Words:
- “Recovery and rebuilding”
- “Making Puerto Rico resilient”
- “Modernizing infrastructure”
The Behavior:
- Fiscal control board imposed before hurricane
- Hurricane provided cover for predetermined cuts
- Public schools closed (300+), charter school expansion
- PREPA (public utility) privatization pushed
- Disaster contracts to mainland firms, not local
- “Opportunity zones” created for tax-advantaged investment
- Crypto investors moved in for tax haven benefits
- 400,000+ residents left island (14% population decline)
Detroit Bankruptcy (2013):
The Words:
- “Necessary restructuring”
- “Saving the city”
- “Protecting essential services”
The Behavior:
- Pensions cut 20-30% (retirees who worked decades)
- Public assets sold (Belle Isle, water system attempted)
- Emergency manager appointed, democracy suspended
- Downtown gentrification while neighborhoods collapsed
- Quicken Loans/Dan Gilbert acquired vast downtown holdings
- Private equity bought distressed residential properties
- Two-tier city: downtown boom, neighborhoods abandoned
COVID-19 Pandemic (2020-2022):
The Words:
- “Small business support”
- “Keeping economy afloat”
- “We’re all in this together”
The Behavior:
- PPP loans to large corporations (not small businesses)
- Stock market soared while unemployment spiked
- Billionaire wealth increased $2 trillion
- Small business failures: 200,000+ permanent closures
- Corporate consolidation across industries
- Commercial real estate acquired at distressed prices
- Musk wealth went from $27B to $200B+ (7x increase)
Watch for this pattern:
- Crisis → Emergency powers → Normal protections suspended → Corporate acquisition → Original stakeholders displaced
This happens regardless of which party controls government. The mechanism is structural, not political.
International: China and Uyghur Population
The Words:
- “Vocational training centers”
- “Counter-terrorism measures”
- “Economic development”
- “Poverty alleviation”
The Behavior:
- Mass detention (1-3 million people)
- Forced labor documented
- Cultural sites destroyed
- Birth rates in region collapsed
- Surveillance state implementation
- Population transfer programs
- Economic integration favoring Han Chinese settlement
The Pattern:
- Incremental displacement (strategic uninhabitability)
- Cultural and economic pressure
- Surveillance and control mechanisms
- Gradual population replacement
- Plausible deniability maintained
- International constraints ignored
Not making moral equivalence. Noting mechanism pattern.
International: Russia and Ukraine Rhetoric
The Words (Pre-Invasion):
- “Just military exercises”
- “No plans to invade”
- “NATO expansion is the real threat”
- “Protecting Russian speakers”
The Behavior:
- Troop buildups at border (100,000+)
- Medical supplies positioned forward
- Blood banks moved to field positions
- Logistics infrastructure deployed
- Disinformation campaigns intensified
- Cyber attacks on Ukrainian infrastructure
The Constraint Model said:
- “Invasion too costly”
- “International isolation would be severe”
- “Economic sanctions would bite”
- “Military occupation unsustainable”
The Terrain Model observed:
- Behavior indicated preparation for invasion
- Pattern matched historical precursors
- Words contradicted observable actions
- Timeline compressed despite denials
Result: Invasion occurred. Terrain model was correct. Constraint model assumed constraints would prevent action.
What These Examples Share
Across administrations, across countries, across contexts:
1. Words-Behavior Mismatch
- Official explanations contradict observable actions
- Narrative manages perception, not reality
- Constraints invoked rhetorically, ignored practically
2. Exception Becomes Routine
- “One time emergency measure”
- Repeated in next crisis
- Eventually standard practice
- Original justification forgotten
3. Incremental Normalization
- Each step small enough to avoid triggering resistance
- Cumulative effect transforms system
- By time people notice, too late to reverse
4. Plausible Deniability Maintained
- Legal frameworks provide cover
- “Following the rules” while violating spirit
- Technicalities substituted for accountability
5. Constraints Treated as Obstacles, Not Limits
- International law referenced, not followed
- Domestic rules bent through interpretation
- Accountability mechanisms circumvented
- Enforcement assumed absent, usually correctly
6. Pattern Repeats Regardless of Party/Leader
- Mechanisms transcend individuals
- Structures enable behavior
- Incentives drive actions
- Power consolidates incrementally
This isn’t about Democrat vs. Republican. It’s not about America vs. other countries. It’s about how power operates when constraints weaken and accountability fails.
The pattern is the point. Not which team is doing it.
Two-Bound Forecasting: How to Track Both Models Simultaneously
This two-bound method is most predictive in loosely coupled environments, where synchronized outcomes can emerge without centralized planning.
When you see the pattern – words diverging from behavior, constraints being treated as obstacles – you need a framework that tracks both possibilities without committing too early to either.
The Method: Hold Two Forecasts at Once
Bound A: Constraint-Governed World
- Assumes enforcement mechanisms work
- Assumes costs (legal, reputational, economic) will bite
- Assumes institutional friction slows or stops behavior
- Assumes norms and precedent matter
Bound B: Exception-Governed World
- Assumes constraints are treated as obstacles to route around
- Assumes enforcement lags or doesn’t come
- Assumes institutional capture allows behavior to continue
- Assumes precedent gets rewritten by action
Neither bound is “right” initially. You’re tracking which one keeps landing predictions.
CRITICAL LIMITATION: The Bound B Ceiling
Bound B works until it doesn’t. While this model assumes that constraints can be routed around, there is a point where the “Handbook” (Bound A) re-asserts itself through systemic force. This occurs when an actor’s overreach finally triggers a “Hard Wall” that cannot be bypassed.
Tripwires for the Re-Assertion of Bound A
When you are operating in Bound B (the exception-governed world), you must watch for the specific friction points that indicate the “Hard Wall” of Bound A is beginning to re-materialize. These tripwires signal that the environment is no longer tolerating the exception and is forcing a return to the handbook.
- Black Swans: Unpredictable system breaks that even powerful actors cannot route around.
- Triggered Walls: Market collapses or revolutions that occur when the terrain can no longer support the exception.
- Resource Exhaustion: Points where limits become real even for the wealthy and powerful.
- Dependency Activation: Moments when essential partners (such as banks or allies) refuse further comaoperation.
For Example: - Financial Settlement Drag: Payments or settlements that were previously delayed or ignored are suddenly enforced by a third-party audit or court order (the “Economic Weapon” fails to ground the current).
- Dependency Defection: A critical partner (like a bank, a cloud provider, or an insurance carrier) terminates service because the “Reputational Cost” has finally exceeded the “Incentive Gradient”.
- Enforcement Resurgence: Regulatory agencies or law enforcement (who were previously “Idling”) suddenly issue high-consequence findings that cannot be routed around with “Plausible Deniability”.
- Legitimacy Collapse: The “Broadcast Signal” of the kill no longer project’s power but instead triggers a massive, coordinated “Immune Response” from the broader system.
- The Resource Hard-Limit: The actor attempts a “Level 4” displacement but lacks the actual capital or physical logistics to maintain the unlivable terrain, leading to a system-wide “Black Swan” failure.
Tripwires are early warning, not guarantees: If Bound B starts failing and costs suddenly become real (or dependencies bite), the environment has shifted back toward a Bound A reality. You must update your forecast immediately.
How to Use It
Step 1: State Both Forecasts Explicitly
Maritime strikes example:
Bound A Forecast:
- Strikes will be limited to emergency situations
- Boarding attempts will be standard procedure
- Prisoners will be taken when possible
- Evidence will be preserved and displayed
- International law will constrain expansion
- Congressional oversight will limit scope
Bound B Forecast:
- Strikes will become routine counter-narcotics procedure
- Standoff weapons will become standard (no boarding)
- No prisoners taken, destruction preferred
- Evidence destroyed rather than preserved
- Theater will expand beyond initial region
- Legal justifications will be classified
- Scope will expand to other mission sets
Step 2: Set Tripwires for Each Bound
Tripwires that would validate Bound A:
- Strikes decrease after initial period
- Prisoners taken in subsequent operations
- Evidence displayed, trials conducted
- Congressional hearings impose limits
- International pressure causes policy change
Tripwires that would validate Bound B:
- Strikes increase in frequency
- Theater expands (Caribbean → Pacific → other regions)
- Standoff distance increases (less pretense of imminent threat)
- Classification increases (legal memos not public)
- No prisoners taken becomes pattern
- Proposals expand to other contexts (aircraft, etc.)
Step 3: Track Which Tripwires Fire
As events unfold, mark which predictions land:
Bound A: ☐ ☐ ☐ ☐ ☐ (0/5 tripwires) Bound B: ☑ ☑ ☑ ☑ ☑ (5/5 tripwires)
When Bound B consistently outperforms Bound A, update your model.
Step 4: Update Your Planning Assumptions
If Bound B is landing predictions:
- Downgrade constraints from “walls” to “friction”
- Assume behavior will continue unless actually stopped
- Plan for expansion, not limitation
- Prepare for exception to become routine
- Consider exit strategies before trap closes
You’re not being paranoid. You’re being empirical.
Step 5: Watch for Bound B Failure
If Bound B predictions start failing:
- Costs becoming real (sanctions actually bite)
- Dependencies activating (allies refuse cooperation)
- Legitimacy collapsing faster than expected
- Resource constraints binding
- Black swan events disrupting pattern
This means the environment changed. Don’t stay wedded to Bound B thinking.
Note: Tripwires tell you what to watch. The missing skill is grouping. In loosely coupled environments, separate incidents can belong to the same mechanical bundle even when each is individually deniable. For a practical grouping method (the Bundle Test) and the Two Clocks enforcement model, see Field Note: Loosely Coupled Power Grabs.
Universal Tripwires: What to Watch For Across Any Context
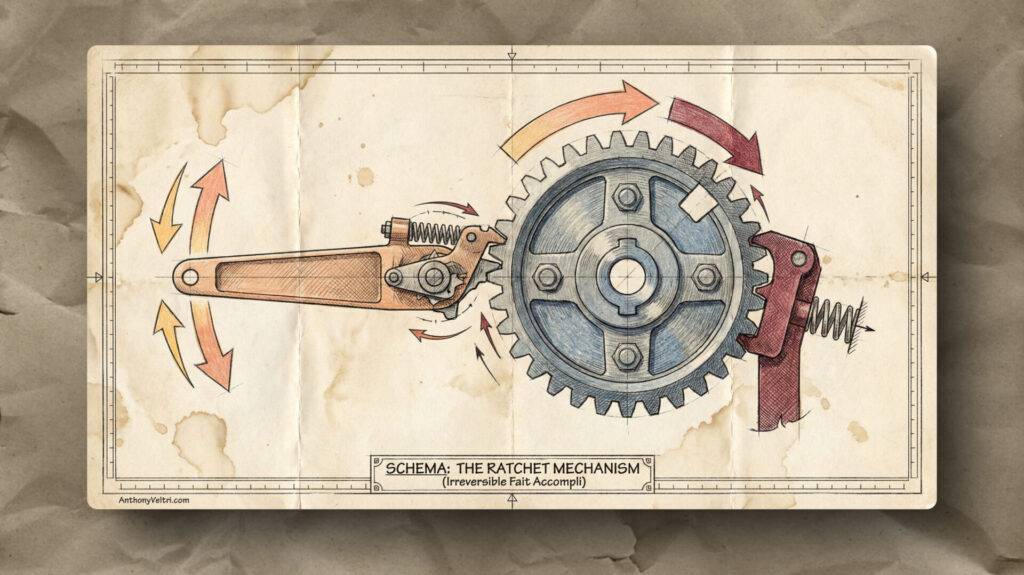
The Resistance Differential: Why the Alarm Stays Dark
In the Practitioner Archive, we use a resistor symbol to represent the inherent “cost” of operating outside of established norms. While the “Handbook” path (the fuses) is intact, it offers the path of least resistance. The institutional fuses shunt the “Current of Intent” away from the public alarm.
The system doesn’t “choose” the alarm (it is forced into it). Once the final 50A shunt of Selective Rules is destroyed, the resistance of the alarm path becomes lower than the infinite resistance of the blown fuse gap. The state change is complete: the system normalizes the exception because the “Normal” path no longer exists.
These tripwires indicate you’re in an exception-governed environment. If 2-3 fire in a short window, shift to Bound B thinking.
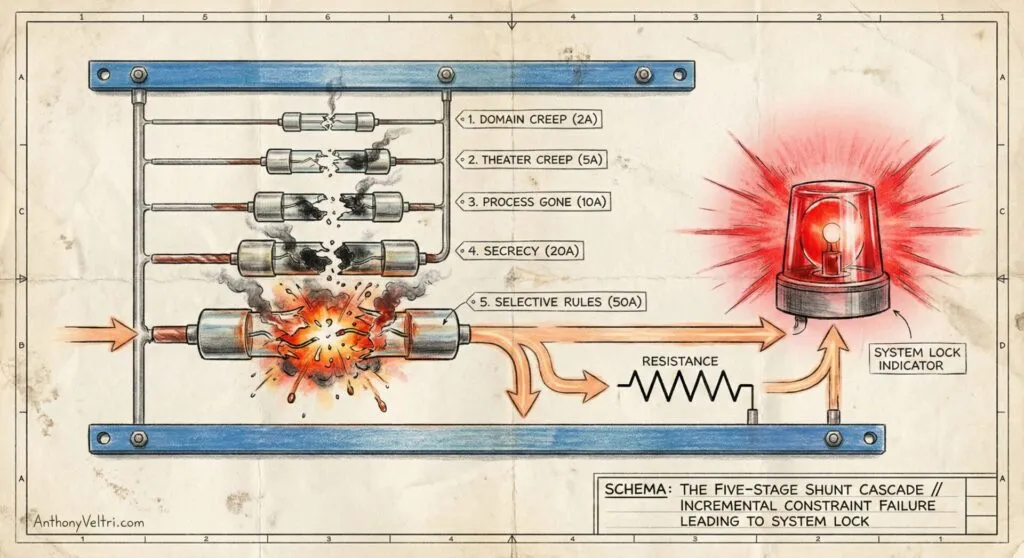
The Resistance Differential: This diagram shows how institutions fail when they stop following the rules and start following the power. Think of the “Handbook” (the laws and procedures) as a series of Safety Valves (the five fuses).
The Path of Least Resistance: As long as these safety valves are intact, the system’s energy flows through them easily. This is the “normal” way of doing business: it’s low-friction, predictable, and keeps the “System Normal” light glowing green.
The High-Cost Alternative: In parallel, there is another path: the “Terrain.” This path is blocked by a heavy Resistor, which represents the massive political, legal, and reputational costs of breaking the rules. Because it’s so “expensive” to go this way, the system ignores it and sticks to the Handbook.
The State Change: The failure happens in a predictable cascade. One by one, the smaller safety valves (Domain Creep, Theater Creep, and Secrecy) which blow under pressure. The system holds together until the final, largest valve, “Selective Rules,” is vaporized.
At that exact moment, the “Normal” path is gone. It isn’t just closed; it has been replaced by a dead end. The energy has no choice but to pay the high cost of the Resistor and flood into the “Failure State” circuit. The resulting red strobe isn’t a warning that something might go wrong, it’s a positive signal that the old system has been destroyed and the Terrain is now the only reality left.
Tripwire 1: Domain Creep
What to watch for: The behavior expands to new domains.
Examples:
- Maritime strikes → Proposals for aircraft interdiction
- Drone strikes in war zones → Drone strikes in non-combat countries
- Surveillance of foreign nationals → Surveillance of citizens
- Emergency powers for pandemic → Emergency powers for other crises
Why it matters: Each domain expansion normalizes the behavior further. Tests whether anyone will stop it.
Watch for this when: Initial justification was narrow (“only in this specific case”) but application keeps broadening.
Tripwire 2: Theater Creep
What to watch for: The behavior expands to new geographic areas or new target sets.
Examples:
- Caribbean operations → Pacific operations → Global operations
- One city’s private equity buyout → Multiple cities simultaneously
- Specific region’s surveillance → Nationwide surveillance
- One disaster’s predatory acquisition → Pattern across all disasters
Why it matters: Geographic expansion tests limits. If no one stops it in Theater A, it spreads to Theater B, C, D.
Watch for this when: Behavior that was supposedly location-specific starts appearing elsewhere with same justification.
Tripwire 3: Process Substitution
What to watch for: Due process steps disappear. “Effects” publicized while accountability steps vanish.
Examples:
- Strikes shown, but no trials
- Acquisitions completed, but no regulatory review
- Decisions made, but no public deliberation
- Effects visible, but process invisible
Why it matters: Process is how accountability happens. When process disappears but outcomes increase, you’re seeing power without accountability.
Watch for this when: You see results but can’t see how decisions were made or who made them.
Tripwire 4: Secrecy as Strategy
What to watch for: Classification increases. Legal justifications move out of public view. Fewer records, more ambiguity.
Examples:
- Legal memos classified
- Decision-making processes confidential
- Data collection hidden
- Contractor identities masked
- Financial transactions opaque
Why it matters: Secrecy prevents accountability. What you can’t see, you can’t challenge.
Watch for this when: Information that was previously public becomes classified, or new programs launch with no public justification.
Tripwire 5: Selective Enforcement
What to watch for: Rules apply differently to different actors. Insiders exempt, outsiders punished.
Examples:
- Whistleblowers prosecuted, actual crimes ignored
- Small businesses bankrupted for violations, corporations get warnings
- Citizens subject to surveillance, officials exempt
- Protesters arrested, government violence unpunished
Why it matters: Selective enforcement means rules are tools of control, not universal standards.
Watch for this when: The same behavior gets very different responses depending on who does it.
Tripwire 6: Survivor Treatment Shift
What to watch for: How people involved are treated changes. Witnesses disappear. Testimony prevented. No-rescue becomes policy.
Examples:
- Maritime: Secondary attacks targeting survivors on flotsam
- Corporate: Bankruptcy weaponized to silence claimants
- Whistleblowers: Prosecution rather than protection
- Journalists: Arrest rather than access
Why it matters: When survivors become problems to eliminate rather than people to protect, you’re seeing systematic violence.
Watch for this when: Policy shifts from “protect and preserve” to “eliminate and destroy.”
Tripwire 7: Mainstream Target Broadening
What to watch for: Behavior initially directed at “edge cases” starts hitting normal people/entities.
Examples:
- “Only terrorists” → “Suspected associates” → “Anyone in the area”
- “Only abandoned properties” → “Distressed sales” → “Any property we want”
- “Only foreign enemies” → “Dual nationals” → “Citizens who dissent”
Why it matters: Expansion from edge to mainstream shows testing complete. Now standard practice.
Watch for this when: You initially dismissed because “that only affects bad guys” but now it’s affecting people like you.
Anti-Paranoia Guardrails: How Not to Become a Conspiracy Theorist
Terrain thinking can drift into paranoid thinking if you don’t maintain standards.
Use these checks to stay calibrated:
Guardrail 1: Base Rate Check
Question: How common is this behavior historically? What changed?
Application:
- Don’t treat common behavior as exceptional
- Don’t treat new behavior as identical to past
- Understand frequency and context
Example:
- Governments always classify some things → Normal
- Government dramatically increases classification → Notable
- Government classifies legal justifications that were previously public → Significant shift
Guardrail 2: Dependency Check
Question: What systems does the actor still need? What would constrain them?
Application:
- Even powerful actors depend on others
- Banking, alliances, infrastructure, legitimacy
- True power requires cooperation
Example:
- Russia can invade Ukraine, but:
- Needs China not to oppose
- Needs domestic support to sustain
- Needs economy to fund military
- These dependencies create real constraints
Guardrail 3: Cost Check
Question: Are they paying real costs or only rhetorical costs?
Application:
- Rhetoric is cheap
- Economic sanctions, alliance fractures, market responses are real
- Distinguish between criticism and consequences
Example:
- International condemnation → Rhetorical cost (low)
- Lost trade relationships → Real cost (medium)
- Currency collapse → Real cost (high)
- Military defeat → Real cost (severe)
Guardrail 4: Alternative Explanations
Question: What’s the simplest explanation consistent with the facts?
Application:
- Prefer incompetence over malice when both fit
- Prefer bureaucratic dysfunction over conspiracy
- Prefer aligned incentives over coordinated planning
- But don’t dismiss patterns when simpler explanations fail
Example:
- One contractor bankruptcy → Maybe bad luck
- Multiple contractor bankruptcies with same firm → Pattern
- Pattern includes delay tactics, legal harassment → Strategy
- Strategy across multiple firms → Structural
Guardrail 5: Signal Stacking
Question: Do we have multiple independent indicators or one loud anecdote?
Application:
- One incident is an anecdote
- Pattern across multiple incidents is data
- Pattern across multiple domains is system
- Independent sources strengthen signal
Example:
- One news story about maritime strike → Anecdote
- Multiple strikes with same pattern → Emerging pattern
- Pattern plus theater expansion plus classification increase plus legal justification changes → System shift
Use all five guardrails. When multiple guardrails fail to explain away the pattern, trust the pattern.
What This Field Note Cannot Do
Be honest about limitations:
If you’re already locked into a Level 3 or 4 environment as the target, this field note won’t save you.
Level 3 (Economic Weapons):
- If you’re being lawfared into bankruptcy
- If resource asymmetry is crushing you
- If legal system is the weapon being used against you
Creating “friction” just delays the inevitable. You don’t have resources to fight. Engaging legally = stepping into their trap.
Level 4 (Strategic Displacement):
- If you’re in incremental displacement pattern
- If economic pressure making your area unlivable
- If you can’t afford to stay
Pattern recognition doesn’t stop the displacement. Seeing it coming doesn’t give you resources to resist.
What this field note DOES provide:
1. Early Warning
- See pattern before most people
- Tripwires fire before you’re locked in
- Time to exit if you recognize early enough
2. Model Updates
- Stop being surprised
- Forecast based on terrain, not handbook
- Understand what’s actually happening
3. Exit Timing
- Know when to disengage
- Don’t wait for constraints to bite
- Don’t trust process when process is captured
The value is in seeing the shadow before the vulture lands.
If the vulture has already landed and is actively stripping the carcass, observation doesn’t help. You needed to exit before this point.
Last Updated on January 18, 2026