Why resilience cannot be bolted on and only appears when the system is aligned at every layer #
This doctrine argues that resilience is the result of getting all the other patterns right.
This page is a Doctrine Guide. It shows how to apply one principle from the Doctrine in real systems and real constraints. Use it as a reference when you are making decisions, designing workflows, or repairing things that broke under pressure.
You cannot “add resilience.” You must architect conditions where it emerges. #
Most organizations want resilience.
Few understand what it actually is.
They try to add resilience with:
- new tools
- redundancy
- new processes
- new rules
- more staff
- more checklists
These help only a little.
None of them create true resilience.
Resilience is not a thing you add.
Resilience is a thing that emerges when the entire system is aligned.
Lived Example: The activation that “should have” collapsed but didn’t #
During one hurricane season, multiple failures happened at once:
- partner feeds lagged
- a regional hub lost connectivity
- authentication tokens expired
- an upstream server crashed
- a field team went offline
- weather shifted faster than models predicted
By all logic, the mission picture should have collapsed.
But it did not, because:
- we had degraded mode behavior
- we had caching
- we had partial layer rendering
- we had clear intent
- we had distributed decisions
- we had tolerant ingest
- we had partners acting independently
- we had a harmonization layer that accepted differences
Resilience did not come from one feature.
It came from the interaction of many aligned patterns.
Resilience emerged.
Business Terms: What resilience actually is #
Resilience is:
- the ability to function when things break
- the ability to adapt when conditions shift
- the ability to preserve mission tempo
- the ability to maintain alignment under stress
- the ability to self correct
- the ability to continue providing value under degraded truth
Resilience does not come from:
- one tool
- one policy
- one team
- one fix
- one feature
Resilience is the outcome of the entire system behaving coherently.
System Terms: Resilience as an emergent property #
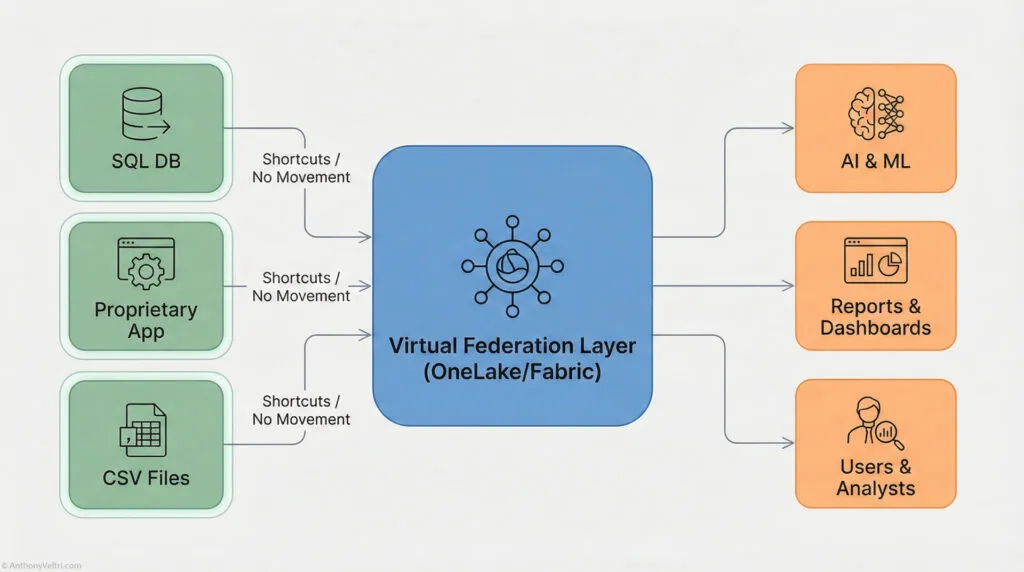
In system language, resilience is emergent when:
- coupling is low
- boundaries are clear
- interfaces are governed
- fallback paths exist
- synchronization is optional
- update delays are tolerated
- decision making is distributed
- constraints are visible
- intent is strong
- innovation happens at the edge
- systems degrade gracefully
One feature does not produce this.
Many small patterns interacting produce it.
Resilience is not a module.
It is a state.
Why “Bolted On” Resilience Fails #
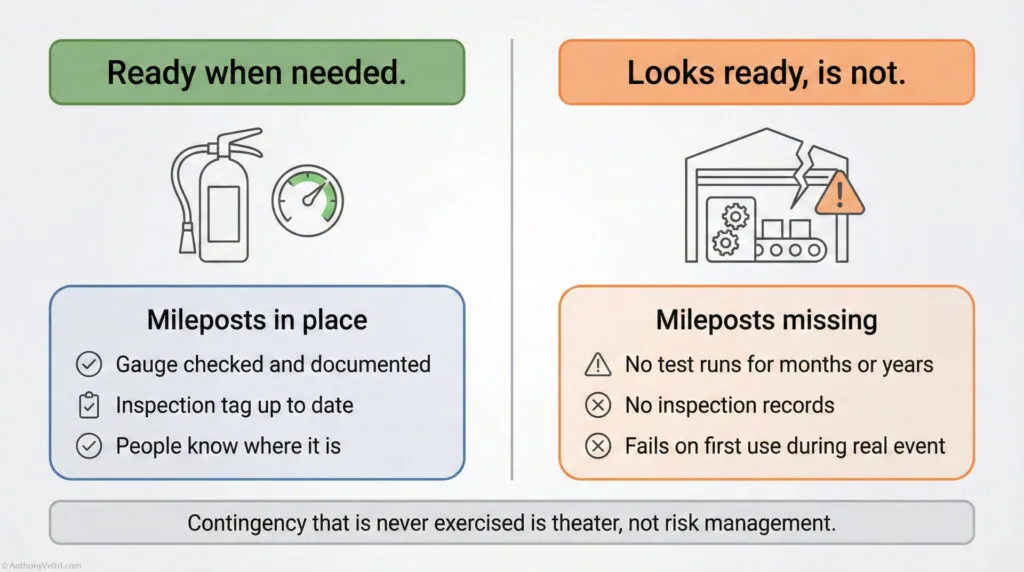
Business perspective #
Organizations try to add resilience as a late-stage patch:
- add a redundant system
- add more staff
- add more reviews
- add stricter rules
- add more documentation
These produce rituals, not resilience.
The system still breaks because the underlying structure is brittle.
System perspective #
Bolt on resilience fails because:
- redundancy without alignment still fails
- failover without contracts still fails
- backups with mismatched schemas still fail
- untested fallback paths still fail
- extra tools increase complexity
- patches increase coupling
- dependencies multiply
Resilience cannot be layered onto a brittle structure.
It must be designed into the structure itself.
Why Emergent Resilience Succeeds #
Business perspective #
A system with emergent resilience:
- does not rely on heroics
- does not stall under imperfect conditions
- makes better decisions with less information
- reduces escalation
- protects leadership from overload
- converts uncertainty into manageable variation
- increases trust from partners
- reduces operational anxiety
This is not theory.
This is lived experience from every major activation you have supported.
System perspective #
A system with emergent resilience:
- isolates failures
- maintains partial functionality
- compensates for upstream drift
- accepts asynchronous updates
- adapts to varied partner maturity
- falls back instead of failing
- contains errors
- heals when nodes recover
- preserves enough accuracy to act
This behavior cannot be built in one place.
It emerges across places.
Business Example: The continuity that emerged from many small design choices #
During a multi-day incident:
- field updates were inconsistent
- partner feeds drifted
- satellite imagery lagged
- analysts were overloaded
- security tokens rotated at the wrong time
But because:
- the caching was solid
- the UI could display partial truth
- the harmonization layer was tolerant
- analysts understood intent
- distributed decisions were authorized
- team boundaries were clear
The mission picture never went down.
No single feature caused this.
The interaction of patterns caused it.
System Example: iCAV’s resilience came from the structure, not a module #
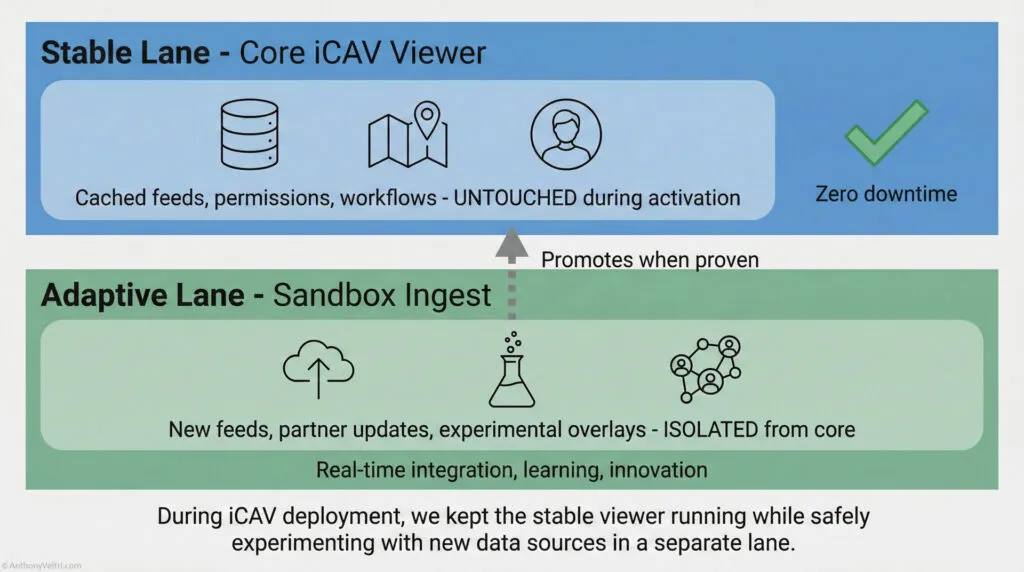
In iCAV, resilience arose because:
- ingest was tolerant
- connectors were loosely coupled
- refresh rates varied safely
- slow feeds did not block fast ones
- failure domains were isolated
- caching preserved useful truth
- interfaces had owners
- the viewer did not require global synchronization
- degraded mode was intentional
- partial data still displayed
None of these on their own produce resilience.
Together they produced a system that survived real world chaos.
This is emergent behavior.
Architect Level Principle #
As an architect I do not add resilience.
I design the conditions for resilience to emerge.
Resilience comes from alignment across people, process, data, and technology.
It is the system behaving as a coherent whole under stress.
Twenty-Second Takeaway: #
“Resilience is not a feature. It is an emergent property of a well-designed system. You cannot bolt it on. You must design for clear intent, distributed decisions, tolerant ingest, loose coupling, and graceful degradation. When these align, resilience appears naturally.”
Cross Links to Other Principles #
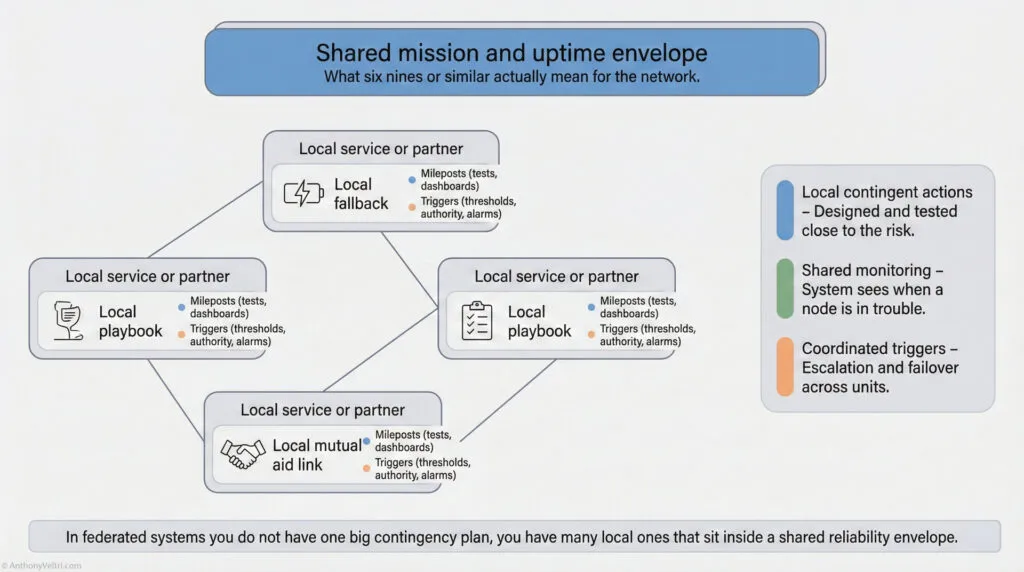
Emergent resilience is the convergence of:
- Degraded operations
- Useful interoperability
- Federation
- Two-lane systems
- Interfaces and ownership
- Preventive and contingent action
- Distributed decisions
- Clear intent
- Technical debt as leadership signal
- Architecture accelerates
This principle is one of the doctrinal pillars.
Doctrine Diagnostic – For Reflection: #
Ask yourself:
Are you trying to add resilience?
Or are you designing the conditions where resilience can appear?
One will fail.
One will create the system you actually want.
Field notes and examples #
- Field Note: Defining “Operator”
- The Scalpel vs. The Swiss Army Knife: When Solo Integration Beats Federation
- Disposable Pixels (UI) On A Durable Substrate
- Systems Built On Heroics Are Brittle
- You Remember My Values, But Not Yours
- Hoover Dam Lessons: “Proudly Maintained By Mike E.”
- When You Choose Integration over Federation On Purpose
- When You Become The Interface: A System “Tell” In Disguise
Last Updated on February 22, 2026