What this route does in 10 minutes
You’ll understand why authorization context degrades during disconnection, identify where trust boundaries fail in your workflows, and know how to preserve authorization envelopes across asynchronous operations.
Start here: Three fast questions
Before you dive in, orient yourself:
- Do workflows disconnect? Do users work offline, across systems, or asynchronously?
- Does context travel? When authorization happens in one place, does it persist properly elsewhere?
- Is audit anxious? Do you worry about proving who did what, when, under what authority?
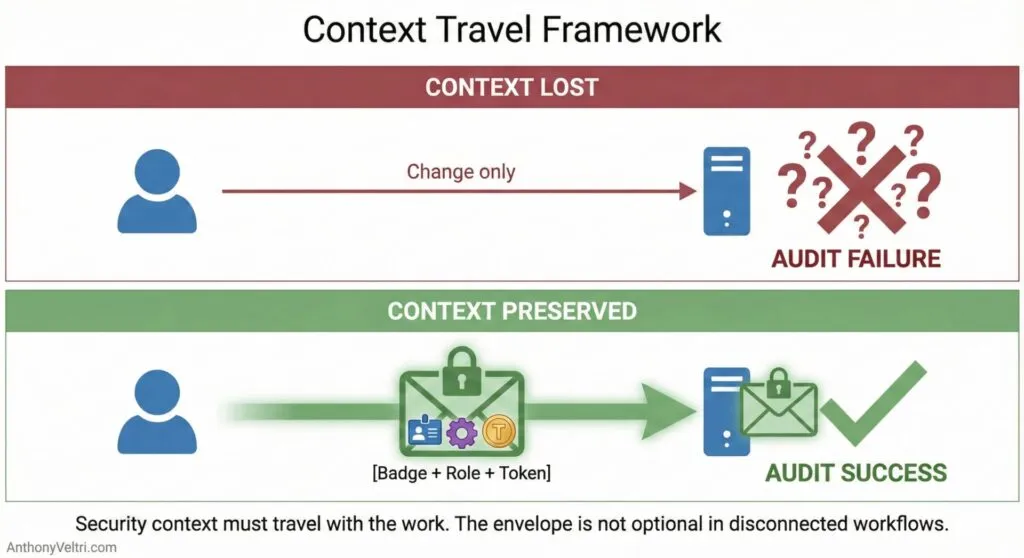
If authorization context gets lost during disconnected or asynchronous work, you’re in the right route.
Quick diagnostic
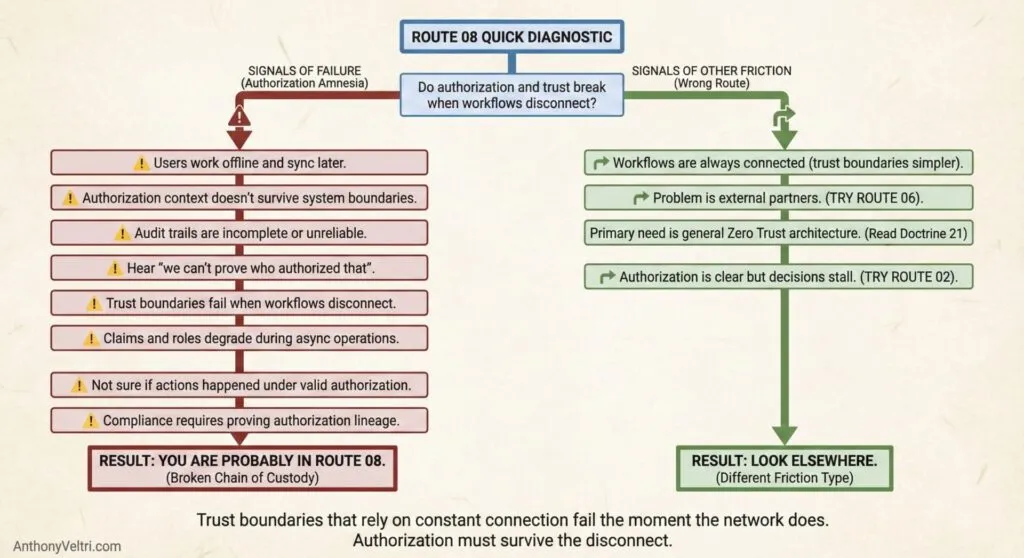
You are probably in this route if:
- Users work offline and sync later
- Authorization context doesn’t survive system boundaries
- Audit trails are incomplete or unreliable
- You hear “we can’t prove who authorized that”
- Trust boundaries fail when workflows disconnect
- Claims and roles degrade during async operations
- You’re not sure if actions happened under valid authorization
- Compliance requires proving authorization lineage
You are probably NOT in this route if:
- Workflows are always connected (trust boundaries still matter, but simpler)
- The problem is external partners (try Route 06)
- You need zero trust architecture (read Doctrine 21, but also stay here)
- Authorization is clear but decisions stall (try Route 02)
Doctrine and Annex anchors
These pieces define the principles and provide the models:
Doctrine 21: Zero Trust Is A Trust Model, Not A Card “Type” Foundational principle: trust boundaries exist everywhere, and authorization context must be explicit and verifiable at every boundary.
Doctrine 21 Companion: Claims, Roles, and Entitlements in Microsoft 365 Practical implementation of zero trust principles using modern identity systems, showing how claims travel (or fail to travel) across boundaries.
Doctrine 23: Loop Closure as Load-Bearing System Infrastructure Why closing authorization loops matters for audit and compliance, and how disconnection creates open loops that create risk.
Field Notes that show the failure mode in the wild
These cases show what happens when authorization context degrades and how to preserve it:
Field Note: Session Hijacking in 1999: What A URL Bug Taught Me About Trust Models Story of discovering client-side trust assumptions in BoulderingGear.com shopping cart, showing how trust boundaries fail and why zero trust matters.
Field Note: Disconnected Editing Is Not a GIS Feature. It Is a Survival Pattern. Why field workers need to work offline, how authorization context must survive disconnection, and what happens when it doesn’t.
Field Note: Respect The Envelope: Why Legal Is Not Always Safe How operating at the legal edge without margin creates brittleness, and why authorization envelopes need slack for operational reality.
Choose your situation
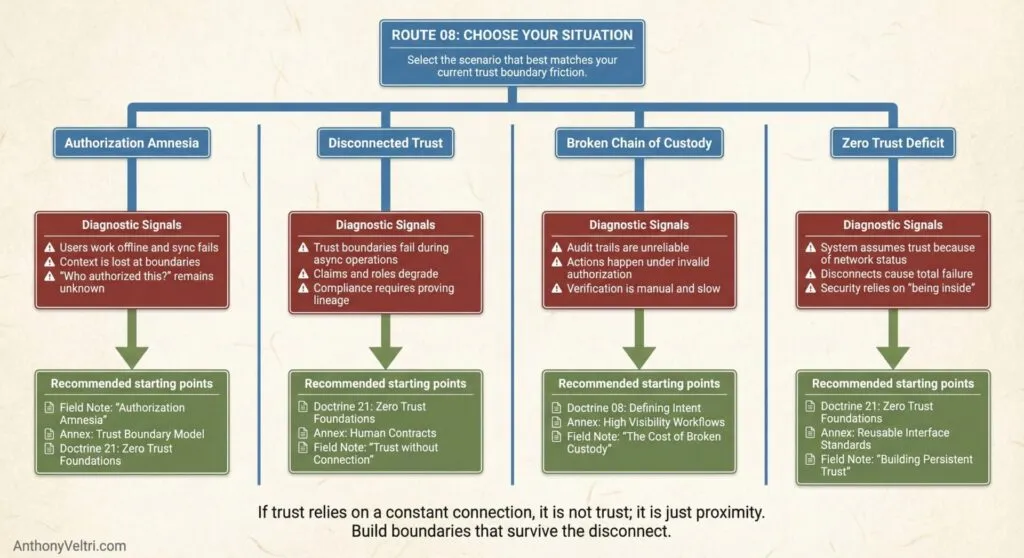
Pick the scenario that most closely matches your context:
Scenario A: Offline work, uncertain authorization
Signals:
- Field workers operate disconnected
- Authorization happens before disconnect
- When they sync back, you can’t prove authorization was valid
- Audit asks “how do you know they were authorized at time of action?”
- You’re not confident in authorization lineage
Start with:
- Field Note: “Disconnected Editing” (see the operational pattern)
- Doctrine 21 (trust boundary principles)
- Doctrine 23 (closing authorization loops)
Scenario B: Cross-system workflows lose context
Signals:
- Authorization happens in System A
- Work happens in System B
- Context doesn’t travel properly
- You rely on users to “remember” who authorized what
- Audit trails are incomplete
Start with:
- Doctrine 21 (trust boundaries at every interface)
- Doctrine 21 Companion (how claims travel)
- Doctrine 23 (loop closure requirements)
Scenario C: Trust assumptions never validated
Signals:
- You assume certain things are “secure enough”
- Haven’t explicitly validated trust boundaries
- Client-side trust (user controls authorization context)
- Session management is unclear
- Worried about what audit will find
Start with:
- Field Note: “Session Hijacking 1999” (see client-side trust failure)
- Doctrine 21 (validate every boundary)
- Field Note: “Respect The Envelope” (margin for operational reality)
Scenario D: Audit anxiety about proof
Signals:
- Compliance requires proving authorization
- You’re not confident you can prove it
- Audit trails exist but are incomplete
- Open loops everywhere (started but not closed)
- Authorization happened but can’t demonstrate it
Start with:
- Doctrine 23 (closing loops)
- Doctrine 21 (trust boundaries)
- Doctrine 21 Companion (modern identity implementation)
Scenario E: Not sure which scenario fits
Start with:
- Doctrine 21 (foundational principles)
- Doctrine 23 (loop closure)
- Doctrine 21 Companion (implementation patterns)
- Field Note: “Disconnected Editing” (operational disconnection)
- Field Note: “Session Hijacking” (trust boundary failure)
Recommended default path
If you’re unsure which scenario fits, follow this sequence:
- Doctrine 21: Zero Trust Is A Trust Model (5 minutes) Understand why trust boundaries exist everywhere and must be explicit.
- Doctrine 23: Loop Closure as Load-Bearing Infrastructure (5 minutes) Learn why closing authorization loops matters for audit and compliance.
- Doctrine 21 Companion: Claims, Roles, and Entitlements (10 minutes) See modern implementation of zero trust principles in identity systems.
- Field Note: Disconnected Editing (5 minutes) Understand operational disconnection and authorization preservation.
- Field Note: Session Hijacking in 1999 (5 minutes) See client-side trust assumptions fail in practice.
Total time: 30 minutes from authorization anxiety to explicit trust boundaries.
What to do next
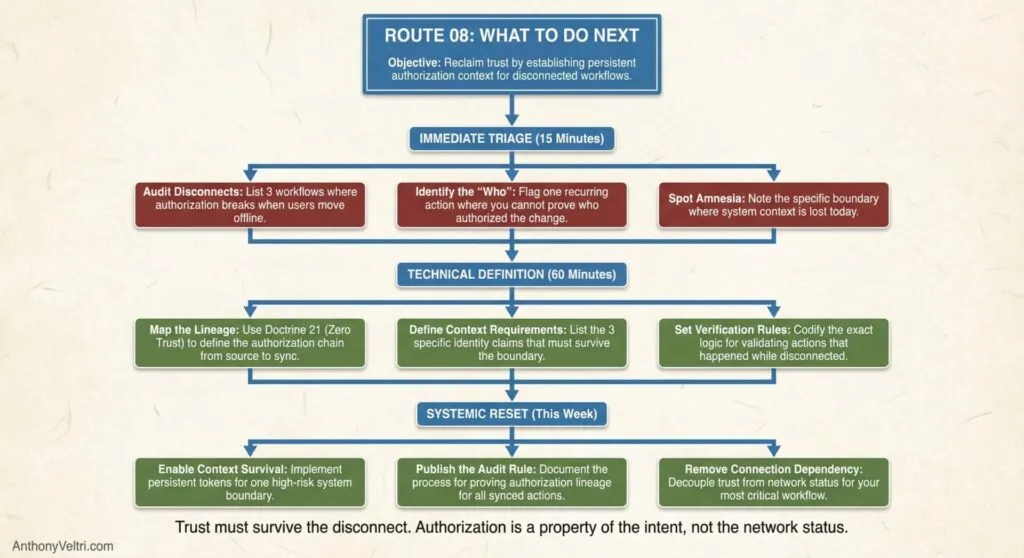
In the next 15 minutes:
- Map your top 5 workflows that involve authorization
- For each one, ask: “Does authorization context survive disconnection or system boundaries?”
- Identify where trust boundaries are implicit (assumed) rather than explicit (validated)
In the next 60 minutes:
- Pick the highest-risk authorization gap
- Document: Where does authorization happen? Where does work happen? How does context travel?
- Identify: Are trust boundaries explicit and validated, or implicit and assumed?
- Draft a one-page plan for closing authorization loops
This week:
- Audit your trust boundaries – where are authorization assumptions instead of validation?
- Design authorization envelopes that survive disconnection
- Implement loop closure for critical workflows
- Document authorization lineage for compliance
- Test: Can you prove who authorized what, when, under what claims?
Optional: Send me 5 sentences
If you want targeted guidance for your specific situation, describe:
- What workflows involve authorization? (online, offline, cross-system)
- Where does context get lost? (disconnection, boundaries, transitions)
- What audit requires? (proof of authorization, lineage, compliance)
- What constraints matter? (technology, budget, timeline, risk)
- What would “closed loops” look like? (desired audit state)